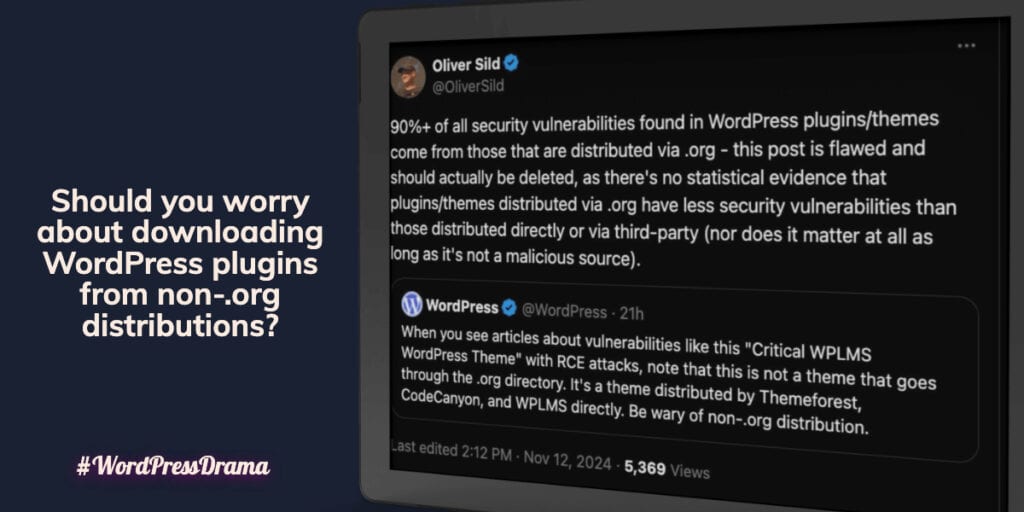
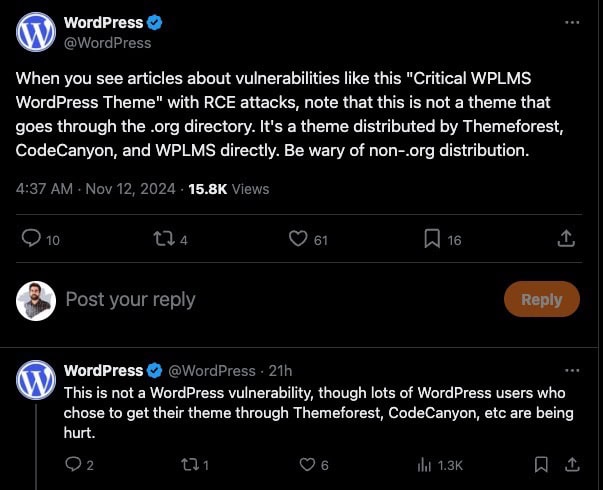
On November 12, 2024, WordPress addressed concerns about vulnerabilities in themes on X, specifically mentioning the “Critical WPLMS WordPress Theme,” which had been associated with remote code execution (RCE) attacks. They stated, “When you see articles about vulnerabilities like this… note that this is not a theme that goes through the .org directory. It’s a theme distributed by Themeforest, CodeCanyon, and WPLMS directly. Be wary of non-.org distribution.” They further clarified, “This is not a WordPress vulnerability, though lots of WordPress users who chose to get their theme through Themeforest, CodeCanyon, etc., are being hurt.”
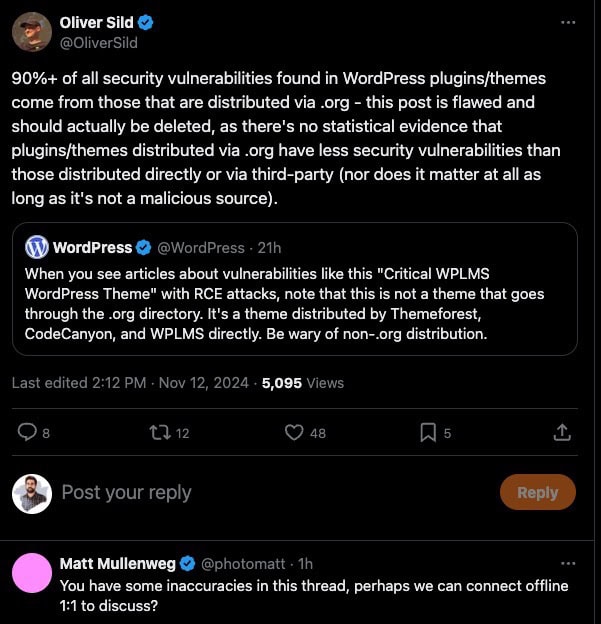
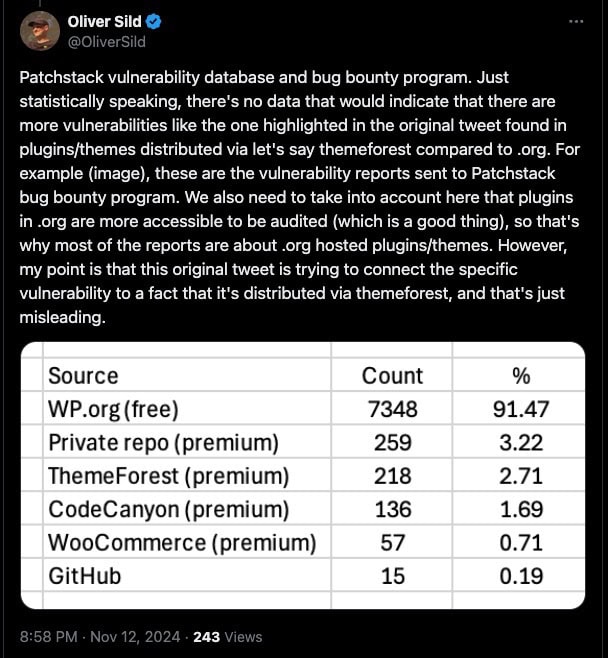
Oliver Sild, the CEO of PatchStack and a well-known security researcher, quickly responded, asserting that this claim was misleading and should be retracted. He stated that “90%+ of all security vulnerabilities found in WordPress plugins/themes come from those that are distributed via .org,” arguing that the original post lacked statistical evidence to support the assertion that .org distributions are inherently safer.
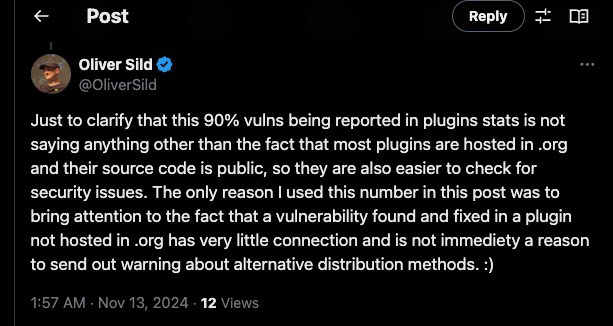
Sild explained that the statistic he referenced does not imply that plugins in the .org directory are more secure. Instead, it reflects that most plugins are hosted there, making their code publicly accessible and easier to audit for security issues. His intent was to clarify that vulnerabilities identified in non-.org plugins do not automatically suggest alarm regarding their distribution methods.
Matt Mullenweg, the founder of WordPress, replied to Sild’s comments, indicating that there were inaccuracies in his thread and suggested a private discussion for further clarification.
Rich Tabor from Automattic questioned the origins of Sild’s 90% claim, recalling his experiences reviewing themes on Themeforest and highlighting the flexibility developers have when uploading themes. In response, Sild cited the Patchstack vulnerability database, indicating no data showed that vulnerabilities like the one mentioned were more prevalent in themes from Themeforest compared to those from .org. He noted that plugins in the .org directory are typically easier to audit, contributing to a greater number of reported vulnerabilities.
Sild emphasized that approximately 50% of known WordPress-related security vulnerabilities have been reported to PatchStack over the past three to four years. He reiterated that just because a vulnerability was found in a plugin with a custom distribution does not mean users should be wary of all non-.org distributed plugins.
This ongoing discourse reveals significant differences in perspectives regarding WordPress security practices. What do you think? Are themes and plugins in the WP repository more secure, or does it not make a difference as Sild suggested? Share your views in the comment section.
For those interested in the full conversation and details, check the X thread discussion here.